I’ve come across this article https://cybersecuritynews.com/windows-user-account-control-bypassed/ recently regarding the UAC bypass using Windows built-int character editor. I will test this proof of concept and make some thoughts about this particular UAC bypass trick.
As Cybersecuritynews noted, “Microsoft’s approach to UAC bypasses remains consistent with historical patterns. Since UAC is designed as a convenience feature rather than a security boundary, the company typically does not issue patches for bypass techniques.” So unfortunately we won’t have any remediations from Microsoft. But we can implement some mitigations ourselves, I will talk about it towards the end of the article.
PoC
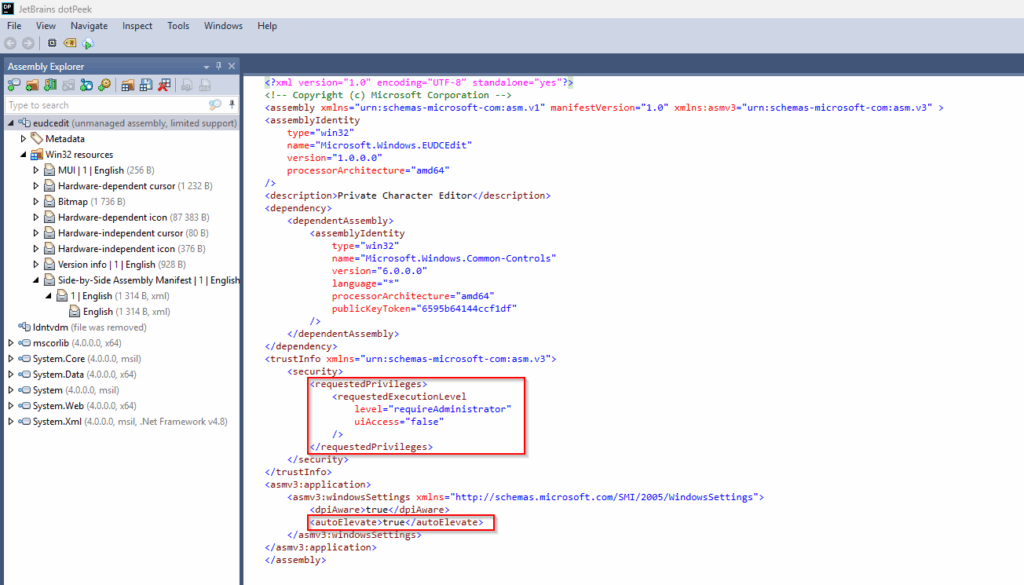
The attack is to leverage the built-in binary eudcedit.exe (Private Character Editor) located in C:\Windows\System32 which is designed to create custom characters and symbols in Windows, also known as End-User Defined Characters (EUDC).
The vulnerability lies in the application’s manifest with the following tags:
<requestedExecutionLevel level="requireAdministrator" />
<autoElevate>true</autoElevate>
These two tags instruct Windows to automatically run it with admin privileges when executed by a user in the Administrators group, especially if UAC is set to a permissive mode like “Elevate without prompting”.
We can confirm that from the application’s manifest.
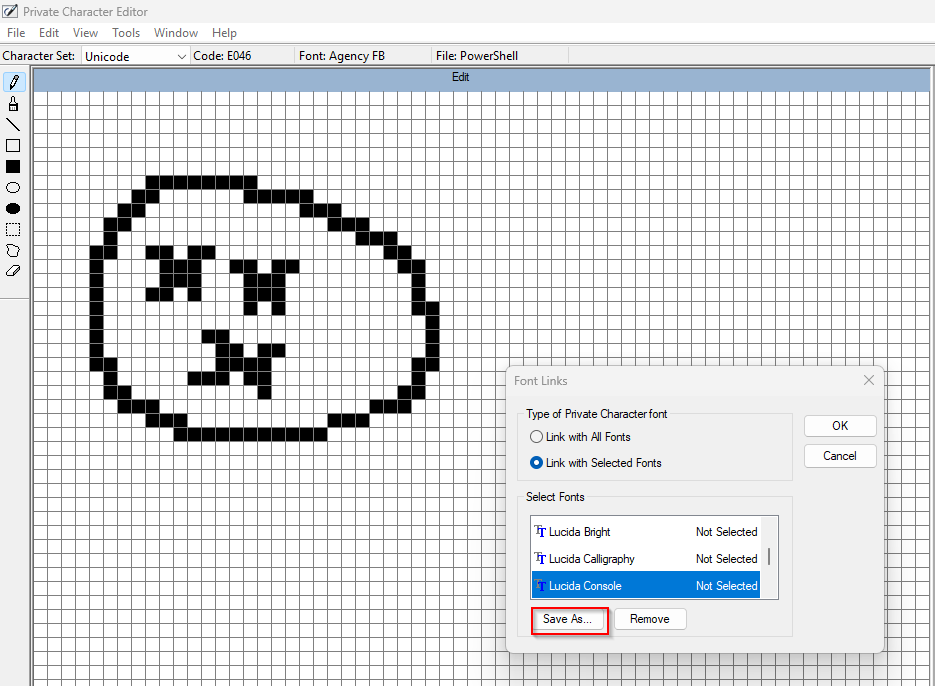
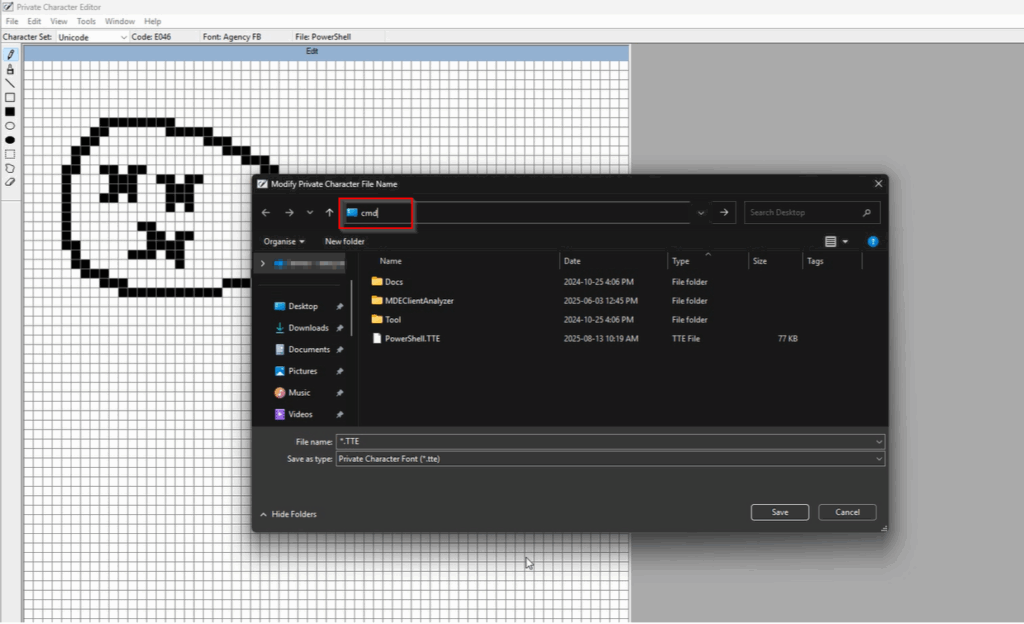
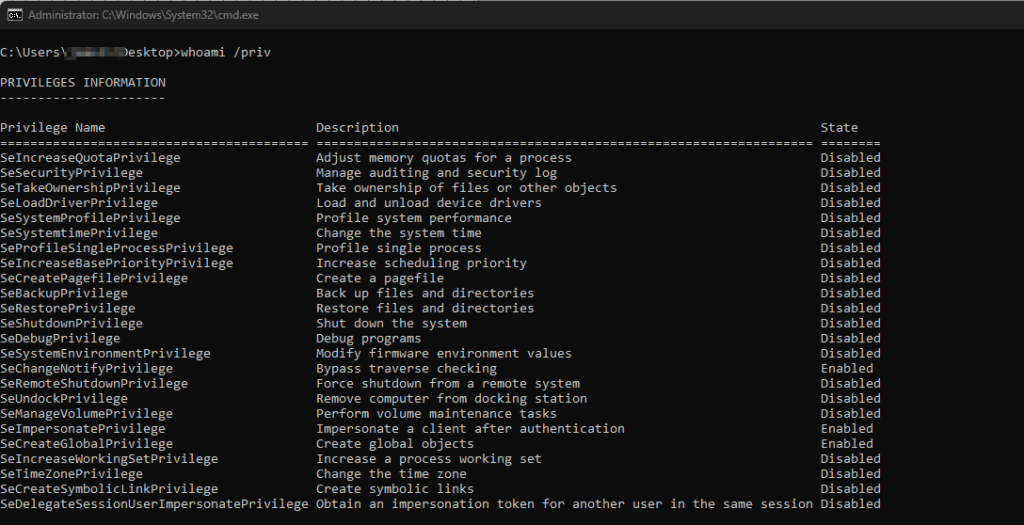
We can exploit it by manipulating the font linking feature. When prompted to save the custom font file, attackers can execute arbitrary commands in the file dialog box such as “PowerShell” or “cmd”. It will then spawn a high-privilege session that inherits the elevated permission from eudcedit.exe.
Afterthoughts
The impact will be minimal if you are just a standard user not in local admin group because it will still prompt you to enter admin credentials.
You might think why is this a threat since if an attacker already has local admin rights, he can pretty much do anything on the local machine such as launching CMD with admin privilege and it doesn’t really matter if UAC is in place or not. Well, these actions could be flagged by modern EDR or AV, but if it’s launched from a trusted binary, it is less likely to be flagged by EDR compared to unknown executables. The absence of a UAC prompt makes the attack stealthy, as users and security tools may not be alerted to the privilege escalation. This makes the bypass a “living-off-the-land” technique, which is harder to detect without behavioral analysis.
Mitigations for eudcedit.exe UAC Bypass
While there are no official patches available, mitigations are possible.
- Set UAC to “Always Notify”: This will ensure all elevation attempts trigger a prompt.
- Restrict eudcedit.exe: Use application control policy (e.g. Defender or AppLocker) to restrict the execution of eudcedit.exe
- Behavioral Analysis Tools: Deploy EDR solutions that detect anomalous behavior, such as eudcedit.exe launching PowerShell or accessing unexpected file paths.
Conclusion
The eudcedit.exe UAC bypass leverages a trusted, Microsoft-signed utility to achieve silent privilege escalation, particularly in environments where users have local admin rights or UAC is misconfigured. While standard users without admin credentials are less directly vulnerable, this bypass can still be part of a broader attack chain, enabling attackers to escalate privileges, deploy malware, or establish persistence. The lack of a Microsoft patch and the technique’s simplicity make it a notable concern for system administrators.